In these assaults, undesirable actors masquerade to be a regarded manufacturer, coworker, or Buddy and use psychological procedures for example creating a perception of urgency to have folks to do what they want.
Insider threats is usually harder to detect than external threats since they have the earmarks of approved activity, and so are invisible to antivirus software, firewalls and also other security remedies that block exterior attacks.
one. Cybercrime incorporates solitary actors or teams concentrating on systems for fiscal attain or to trigger disruption.
To be able to shield and protect against digital assaults, corporations need to create and deploy an extensive security tactic that features equally preventative measures, and also speedy detection and reaction capabilities.
Go through more about ransomware Phishing Phishing assaults are email, textual content or voice messages that trick customers into downloading malware, sharing sensitive information and facts or sending funds to the incorrect people. Most users are aware of bulk phishing ripoffs—mass-mailed fraudulent messages that seem like from a big and dependable brand name, asking recipients to reset their passwords or reenter charge card data.
To lessen your risk from cyberattacks, acquire processes that help you prevent, detect, and reply to an attack. Often patch software and hardware to decrease vulnerabilities and supply crystal clear guidelines in your group, so they understand what actions to get If you're attacked.
Freshservice delivers an extensive suite of IT provider management abilities intended to greatly enhance the performance of modern organizations. With its impressive capabilities, it empowers workforce to seamlessly take care of IT requests in just their current workflows.
Sorts of cybersecurity threats A cybersecurity danger is usually a deliberate try to obtain access to somebody's or Group’s system.
Employ Services Desk Instruments: Invest in services desk equipment and systems that streamline ticketing, tracking, and backbone procedures. These instruments help in running workflows effectively and supply insights into support performance.
In terms of IT support specialist Work specially, you'll find approximately 1 / 4 of one million task postings while in the U.S. on a yearly basis. Around a 3rd of These occupation postings are for entry-level positions, and options are in practically each individual sector.
Cybersecurity will be the exercise of guarding Web-connected systems like hardware, software and data from cyberthreats. It is really utilized by folks and enterprises to shield against unauthorized use of data facilities and various computerized systems.
Believe attacks on governing administration entities and country states. These click here cyber threats normally use several assault vectors to attain their aims.
The suggestions a central IT support function supplies to software and infrastructure groups is really a priceless advantage of IT support. This feed-back enables enhancement initiatives that are crucial to properly running a service successfully after some time.
These assaults can feature little sophistication, but can normally be very sophisticated, where even highly suspicious consumers are fooled.
 Amanda Bynes Then & Now!
Amanda Bynes Then & Now! Richard "Little Hercules" Sandrak Then & Now!
Richard "Little Hercules" Sandrak Then & Now! Tahj Mowry Then & Now!
Tahj Mowry Then & Now! Freddie Prinze Jr. Then & Now!
Freddie Prinze Jr. Then & Now!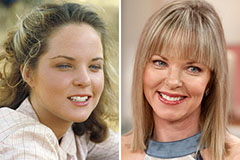 Melissa Sue Anderson Then & Now!
Melissa Sue Anderson Then & Now!