In these assaults, undesirable actors masquerade to be a regarded manufacturer, coworker, or Buddy and use psychological procedures for example creating a perception of urgency to have folks to do what they want.Insider threats is usually harder to detect than external threats since they have the earmarks of approved activity, and so are invisible
 Alana "Honey Boo Boo" Thompson Then & Now!
Alana "Honey Boo Boo" Thompson Then & Now! Kelly McGillis Then & Now!
Kelly McGillis Then & Now! Anthony Michael Hall Then & Now!
Anthony Michael Hall Then & Now!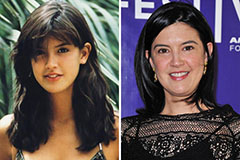 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Shannon Elizabeth Then & Now!
Shannon Elizabeth Then & Now!